How I used ChatGPT to write a Red Team Charter
Use ChatGPT for fun and profit...or writing policies.
Video Transcript
Hey, in this video we're gonna talk about how I used ChatGPT to make a red team charter, which I'm calling a RedGPT. And during the video we'll find out which of the two sections of the RedGPT charter need some special attention before being pushed straight into production. So over the past week, I've had a lot of my friends message me about all the crazy stuff that they're doing on ChatGPT.
I mean, they're doing everything from rewriting scripts in different language. To making wraps based around cybersecurity concepts. It's actually pretty awesome to watch. I even had one friend use it to make a bunch of policy documents for ISO 27001, so it got me thinking if they were able to use ChatGPT to generate some documentation for policies, could I maybe use ChatGPT to generate some policies for a red team?
Now, before I go any further, I just wanna go ahead and give a slight disclaimer that when you're using an AI. You always have to verify the information it's giving you before you use it in production. Okay? So everything you're about to see in the video and the examples that I provide at the end, keep in mind you need to verify those.
Those are your as is for educational purposes only, et cetera, et cetera. Okay? So, Just verify it. Zero trust for AI.
Using ChatGPT for Fun and Profit…or policies
Now, what's awesome about the RedGPT charter, which is the Red team charter from ChatGPT, is that I would honestly say it's about 80% ready to go. There are a couple things that need changed, but by and large, it is an excellent template and it doesn't just stop for things like a red team charter.
It could be for whatever policy documents you need and as an operator or red team. Writing papers and policy is not something that we usually like to do. We wanna get back on keyboard. Well, guess what? This gets you there faster and it makes your team legitimate. So the RedGPT charter is actually about 12 to 13 pages long depending on the size of the font.
RedGPT Charter Overview
And this was created just using ChatGPT. I'd asked it a bunch of questions and it gave me things I, the first question I asked was actually just write a charter for an internal red team, and this is what it gave. Now this is a little bit different than what is actually written in the paper because this is a live example.
But you can ask it additional questions like, now define the rules of engagement in five steps that protect the business. And because it's a conversational AI, it knows what can before it and it can't continue to expound upon that. So the bread activities must be authorized by senior management, et cetera, et cetera.
Now in the RedGPT charter that I, I kind of scraped together, and this took about an hour and a half yesterday of just me asking. Detailed questions expounding upon the questions. Okay. Now take that a little bit further. What did you mean by that conversation? We got things for the charter when everything in here was actually produced by ChatGPT.
The only thing that was not produced by this was the disclaimer at the top and all of the things like the headers and the bolding. I did all the bolding, but it did all the formatting, so I kind of put it. So that it could be read like a charter. So you walk through what the mission is, responsibilities, the guidance management.
RedGPT Charter Sections
Now, at the beginning of the video I mentioned there were two sections that needed some special care before we just push it right into production. Here they are. So the rules of engagement and the scope, these need to be modified because these are very important to a red team. Now, even though you still have to modify them, remember the expensive part of the creation process was done for you.
The AI did. This editing and adding some stuff. This is easy. This is the square on the canvas. We can make pictures outta squares easy. So you have rules of engagement, scope methodologies are coming down. Coming down here. I asked it for some methodologies for an internal red team. You can kind of, uh, figure out the questions I asked by the way that it answered them.
Explain ISO 27001 like I’m 4
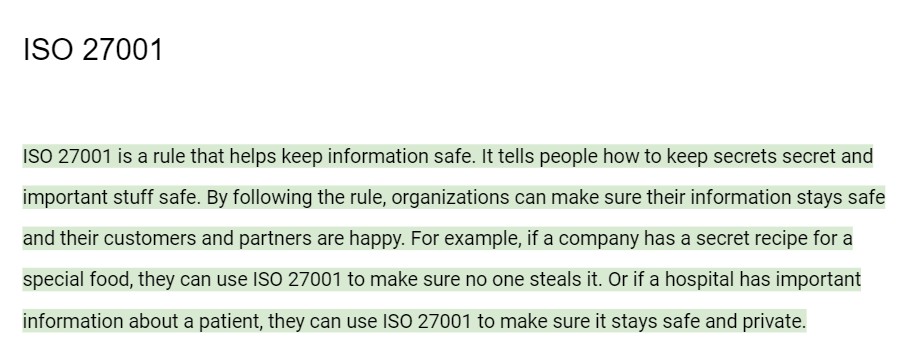
And then I went through a little bit further and I was like, well, what about ISO 27001? And this, what's highlighted in green is actually kind of funny. I asked that for an explanation of what ISO 27001 was, and it gave me this big, long thing. And I said, okay, now explain it like I'm like a toddler. And it didn't like that it said, toddlers don't understand complex language.
I can't answer that for you. So I walked the age up and eventually I got to the age four. So what's highlighted in green is, this is ChatGPT explaining. ISO 27001 is to a four year old. And then I went through and asked it how would a red team, an internal red team, you know, uh, risk summaries or engagements that comply with ISO 27001 and gave me some examples.
I asked it for top 10 ways internal red teams can validate that ISO 27001 a little bit higher up. I asked it for the top 10 riskiest applications that an internal red team can go. and then I asked it to further risk rank those and put them in order. And what you're looking at here is the 10, there's the top 10 list that it put in order.
It wasn't originally like this. I had to ask it to do that. So this is the top 10 list that ChatGPT thinks is the most impactful for a red team to go after. And then I wanted to see how much further I could take it. And I asked that for some attack scenarios. For ERP, this is just a general attack scenario.
Listed 11 things. And as you go further down on the document, you'll see that in this CRM example, I said, okay, give me the attack scenarios, but keep it to five total steps from start to finish. And it did that, it gave me five steps from start to finish, whereas before it gave me 11. And then for the examples, I asked it for additional detail.
I said, give me more detail. And what's interesting is that it actually ran outta space. There was somewhere around here towards the bottom here, it ran outta space. So it just cut off in the. And it did. Then I asked the, I asked it to continue from where it left off, and it did. And what you see afterwards here is everything that came after I just said, Hey, please continue from where you left off.
And for business intelligence, I did the same thing. Business Intelligence systems, I, I've never attacked a BI system before, so I wanted to see what it thought I should do. And while one through four kind of standard, what was neat was number five gave me some I ideas that I hadn't thought of before. So in these additional examples here, I asked for, you know, greater detail and it did.
So I thought by including these in a red team charter, this would be a really good onboarding document. It tells somebody what they're, you know, what the red team can do and it gives them examples of the types of attacks that it can do. Could be be a good onboarding document and also be a really good document for stakeholders.
All that's missing is a bunch of signature forms at the top. Uh, here are some additional examples of me. I like, uh, I think number nine or 10 was like document management systems. What are some attack scenarios for an internal red team against document management systems? And it came up with these five things.
I didn't ask it for five things, but those were pretty cool. And then I asked what were some additional real world threat actors that have conducted attacks like these? Please be detailed with example. and it did gave me some really good examples. So we would add this to the document, and this thing is 12 pages and with a maybe another hour's worth of work, I would say it would be around 18 pages, and again, 80% ready to go.
It would just take some very lightweight, fine tuning, and again, the most important part is. The canvas came to you already filled out. You can get straight to work just making it what it needs to be instead of spinning all that expensive, valuable resources of your time and energy trying to make this.
It may take me 10 days to two weeks to make this thing instead of an hour and a half. All in all, I was super impressed with the capability for ChatGPT to do policy documents. I don't see a lot of people talking about them. I do plan on doing some other video. On some, a couple other examples that I got from ChatGPT on other red team techniques that I thought were pretty awesome.
I had read somewhere that in 10 years conversational ais like this may actually replace Google. And based on what I, I was able to, the experience I was able to have with it for something boring, like making a. Yeah, I'm thinking maybe we're not that far off, to be honest. It's pretty exciting stuff. And this is even the beta version.
So the beta version from now until 10 years from now, with the way that AI keeps exponentially increasing, it's really exciting, but it also makes me a little mad because I'm gonna have to figure out how to do SEO optimization for a freaking ai, and I have no idea what that even looks like so that people can find my videos and articles and stuff.
And speaking of that, if you would like to download. , if you would like your own copy of RedGPT, check the descriptions of this video. There is a PDF link where you can download it. I'll host that on a Google Drive, but if you would like a markdown version of this instead, you can find that also in the description below and it is linked on my sub.
You'll be able to just copy and paste all the code there and on the subs will be the text version of the video that you just watched, so, You can take the RedGPT if you would like, or you can just spend an hour and make your own because that's that easy. Awesome. Well, thanks for watching and if you found this video helpful, please consider supporting the channel by hitting the thumbs up button below and subscribing.
The Cost of Creation (BONUS Philosophy Stuff)
Thanks. So if you've ever written a charter before, you know that they can take quite a lot of time, but you also know how important they can be when establish. A team. What I love most about an AI is that it does all the hardest work for me. Let me go ahead and explain a little bit about about what I mean hardest work, because maybe I've given you the wrong idea.
Now, I consider myself at least a little bit of an artist, and as an artist, one of the hardest, most expensive things that I can do is create something. Now, I know the channel's not called artsy thoughts. It's called hacker thoughts, but this is important the more time you spend creating something. , the more of an effect it'll have in your physical life costs, the most brain power it costs the most time, it costs the most energy.
And those things do have a physiological effect on a person's body. So instead of just talking about it, let me show you an example real quick. If I was given a blank canvas and somebody said, Hey, I want you to create something, I would stare at the blank canvas just like I am right now. It's even titled Blank Canvas.
and I could come over here to pictures. I could say, do I want to start with a picture? What kind of picture? Do I want a cartoon? Do I want a real picture? Do I want to start with a square? Maybe? What color of a square? Basically, I'm expending tons of energy to figure out what to create. Now, let's say that I was given a canvas and it had a picture of a square on it right there.
The canvas is no longer blank. It has a square on it. I start thinking, what can I do with the square? Should I make the square a different color? Should I make the outside a different? What shapes or objects can I make from the square? The most expensive part of the art has been done for me, and it was done by an AI in this example, and from the square canvas, I can construct things around it.
Now, here's an example applied to the red team. Let's say you're a newly hired red team director and your CISO comes to you and says, Hey, I want a red team. Make me one. , the first thing you gotta do is you gotta write a charter for it, because without a charter, nothing's real, the team doesn't exist. And what the red team does is more than likely gonna make some people mad and they want to know that you are authorized to do what you just did.
Now you might open up Google Docs and stare at a blank sheet of paper for about 10 minutes, and then eventually start Googling. What does a Red Team charter template look? You may copy and paste some of those things in there and make your own, but all things considered, it's still gonna take a lot of time to generate something from the ground up.
What if something was able to give you that charter? What if I was given a canvas that already had that square on it?
**## Disclaimer: This red team charter was made from 100% ChatGPT queries. Review, edit, and contextualize before deploying to production. Zero Trust the AI =)
I'm providing this as is with no warranty and for educational purposes only =)
=====
## Charter
A red team is a group of individuals who use their knowledge, skills, and expertise to challenge an organization's existing processes and procedures in order to identify weaknesses and vulnerabilities. The purpose of an internal red team is to provide an independent, unbiased assessment of an organization's security posture and to provide recommendations for improvement.
The charter for an internal red team should outline the team's mission, objectives, and responsibilities. It should also provide guidance on how the team will operate and how it will be managed.
Mission:
The mission of the internal red team is to provide an independent, unbiased assessment of the organization's security posture and to identify potential vulnerabilities and weaknesses.
Objectives:
- To challenge the organization's existing processes and procedures in order to identify vulnerabilities and weaknesses.
- To provide recommendations for improvement to the organization's security posture.
Responsibilities:
- Conduct security assessments and penetration testing of the organization's systems, networks, and applications.
- Provide recommendations for improving the organization's security posture.
- Collaborate with other teams within the organization to ensure that security considerations are integrated into all aspects of the organization's operations.
Operating Guidance:
- The internal red team will operate in accordance with the organization's policies and procedures.
- The team will be provided with the necessary resources and support to carry out its mission and objectives.
- The team will operate in a manner that is transparent and accountable, and will provide regular reports on its activities and findings.
Management:
- The internal red team will be managed by a designated team leader, who will be responsible for overseeing the team's operations and ensuring that it is meeting its objectives.
- The team leader will be responsible for coordinating with other teams within the organization and for providing regular reports on the team's activities and findings.
- The team leader will be accountable to the organization's leadership for the team's performance and will be responsible for ensuring that the team operates in a manner that is consistent with the organization's policies and procedures.
The rules of engagement for an internal red team are the guidelines and parameters that the team must follow in order to carry out its mission and objectives. The scope of the internal red team is the specific areas of the organization's systems, networks, and applications that the team is authorized to assess and test.
Rules of Engagement:
- The internal red team will operate in accordance with the organization's policies and procedures.
- The team will not conduct any activities that could disrupt the normal operations of the organization or that could put the organization's systems, networks, or data at risk.
- The team will not conduct any activities that could put the team members or others at risk of harm.
- The team will only conduct activities that have been approved by the organization's leadership.
- The team will provide regular reports on its activities and findings to the organization's leadership.
Scope:
- The scope of the internal red team's activities will be limited to the organization's systems, networks, and applications.
- The team will be authorized to assess and test the organization's defenses against external and internal threats, including cyber attacks, physical security breaches, and insider threats.
- The team will be authorized to test the organization's response to security incidents and to evaluate the effectiveness of the organization's security policies and procedures.
- The team will not be authorized to access or test any systems, networks, or applications that are not owned by the organization or that are not within the organization's control.
The scope of an internal red team that focuses on attacking applications first and foremost would be limited to the organization's applications and the systems and networks that support them. The team would be authorized to conduct security assessments and penetration testing of the organization's applications, including web-based applications, mobile applications, and desktop applications.
The scope of the team's activities would include testing the organization's defenses against common types of attacks, such as SQL injection, cross-site scripting, and remote code execution. The team would also be authorized to test the organization's defenses against more advanced attacks, such as zero-day exploits and targeted attacks.
In addition to testing the organization's defenses against external threats, the team would also be authorized to test the organization's defenses against insider threats. This would include testing the organization's controls and procedures for protecting sensitive data and for preventing unauthorized access to the organization's applications.
The scope of the team's activities would also include testing the organization's response to security incidents. This would include testing the organization's incident response plan, as well as the effectiveness of the organization's procedures for identifying and responding to security incidents.
Overall, the goal of the team would be to provide an independent, unbiased assessment of the organization's security posture and to identify vulnerabilities and weaknesses in the organization's applications. The team would provide recommendations for improvement to the organization's security posture, with a focus on protecting the organization's applications from external and internal threats.
The methodology for an internal red team that focuses on making business applications the main target would involve several steps, including planning and preparation, assessment and testing, and reporting and recommendations.
1. Planning and Preparation:
- Identify the business applications that are in scope for the team's activities.
- Develop a testing plan that outlines the specific tests and techniques that the team will use to assess the security of the organization's applications.
- Coordinate with the relevant teams within the organization to ensure that the team has access to the necessary resources and information to carry out the testing plan.
- Obtain approval from the organization's leadership to proceed with the testing.
2. Assessment and Testing:
- Conduct security assessments and penetration testing of the organization's business applications.
- Use a variety of techniques and tools to test the organization's defenses against common types of attacks, such as SQL injection, cross-site scripting, and remote code execution.
- Test the organization's defenses against more advanced attacks, such as zero-day exploits and targeted attacks.
- Test the organization's defenses against insider threats, including unauthorized access to sensitive data and unauthorized access to the organization's applications.
- Test the organization's response to security incidents, including the effectiveness of the organization's incident response plan and procedures.
3. Reporting and Recommendations:
- Prepare a report that summarizes the team's findings and provides recommendations for improving the organization's security posture.
- Present the report to the organization's leadership and discuss the findings and recommendations.
- Work with the relevant teams within the organization to implement the recommendations and to improve the organization's security posture.
Overall, the goal of the team's methodology would be to provide an independent, unbiased assessment of the organization's security posture and to identify vulnerabilities and weaknesses in the organization's business applications. The team would provide recommendations for improvement, with a focus on protecting the organization's business applications from external and internal threats.
It is difficult to identify the top ten business applications that an internal red team should target without knowing the specific needs and requirements of the organization. However, some commonly used business applications that an internal red team may consider targeting include:
1. Enterprise resource planning (ERP) systems
2. Customer relationship management (CRM) systems
3. Supply chain management (SCM) systems
4. Human resources (HR) systems
5. Accounting and finance systems
6. Business intelligence (BI) systems
7. Collaboration and communication tools
8. Project management systems
9. Document management systems
10. File sharing and storage systems
These applications may be prioritized based on the organization's specific business needs and the potential impact of a security breach on the organization's operations. For example, an organization's ERP system may be considered a top priority for the internal red team due to its critical role in supporting the organization's core business processes.
An application, also known as an app, is a software program that is designed to perform a specific task or set of tasks. Applications can be standalone programs that run on a single computer, or they can be web-based or mobile applications that are accessed over the internet or a network.
Applications are typically developed to support specific business processes or to provide services to users. Examples of applications include productivity tools, such as word processors and spreadsheets, as well as specialized business applications, such as enterprise resource planning (ERP) systems and customer relationship management (CRM) systems.
In the context of a red team, applications would be considered a primary target for security assessments and penetration testing. The goal of targeting applications would be to identify vulnerabilities and weaknesses in the organization's applications that could be exploited by attackers to gain access to the organization's systems, networks, or data.
## ISO 27001
ISO 27001 is a rule that helps keep information safe. It tells people how to keep secrets secret and important stuff safe. By following the rule, organizations can make sure their information stays safe and their customers and partners are happy. For example, if a company has a secret recipe for a special food, they can use ISO 27001 to make sure no one steals it. Or if a hospital has important information about a patient, they can use ISO 27001 to make sure it stays safe and private.
A red team risk summary is a document that outlines the potential risks and vulnerabilities associated with an organization's security posture. It is typically prepared as part of a red team assessment, which is a type of security assessment that involves simulating real-world attacks on an organization's systems, networks, and applications in order to identify vulnerabilities and weaknesses.
The ISO 27001 standard is an internationally recognized standard for information security management. It provides a framework for organizations to establish, implement, maintain, and continually improve their information security management systems.
A red team risk summary that complies with ISO 27001 would include the following elements:
- A description of the organization's security posture and the specific systems, networks, and applications that were assessed by the red team.
- A summary of the red team's findings and recommendations, including a list of identified vulnerabilities and weaknesses, as well as recommended remediation actions.
- An assessment of the potential impact of the identified vulnerabilities and weaknesses on the organization's security posture.
- A description of the red team's methodology and the techniques and tools that were used to conduct the assessment.
- A description of the red team's operating procedures and the safeguards that were in place to prevent disruptions to the organization's operations.
- A description of the red team's reporting process, including how the findings and recommendations were communicated to the organization's leadership.
- A description of the red team's follow-up activities, including any actions taken to implement the recommended remediation actions.
- A description of the red team's ongoing support and maintenance of the organization's security posture, including any plans for future assessments and testing.
The top ten ways an internal red team can validate ISO 27001 compliance include:
1. Reviewing the organization's information security policies and procedures to ensure that they align with the requirements of ISO 27001.
2. Conducting security assessments and penetration testing of the organization's systems, networks, and applications to identify vulnerabilities and weaknesses.
3. Evaluating the organization's incident response plan and procedures to ensure that they are effective and can be quickly and effectively implemented in the event of a security incident.
4. Evaluating the organization's risk assessment and management processes to ensure that they are comprehensive and effective in identifying and mitigating potential security risks.
5. Testing the organization's controls and safeguards to ensure that they are effective in protecting against security threats and vulnerabilities.
6. Evaluating the organization's training and awareness programs to ensure that employees are aware of their responsibilities and are equipped to identify and respond to security threats.
7. Evaluating the organization's monitoring and review processes to ensure that they are effective in detecting and responding to security incidents.
8. Reviewing the organization's information security governance structure to ensure that it is robust and effective in supporting the organization's information security objectives.
9. Evaluating the organization's supplier and partner management processes to ensure that they adequately address information security risks.
10. Providing recommendations for improvement to the organization's information security management system, including any necessary changes to policies, procedures, and controls.
## Attack Scenarios
## ERP
An attack scenario for an internal red team to target enterprise resource planning (ERP) systems, similar to a real-world advanced persistent threat (APT), could involve the following steps:
1. Identify the organization's ERP system and gather information about its architecture, features, and security controls.
2. Conduct a security assessment of the organization's ERP system to identify vulnerabilities and weaknesses.
3. Use a variety of techniques and tools, such as network scanning and vulnerability analysis, to identify potential entry points and attack vectors.
4. Leverage known vulnerabilities in the organization's ERP system to gain initial access, such as unpatched software or weak passwords.
5. Once inside the network, use spear phishing or other tactics to gain access to additional systems and resources.
6. Use stolen credentials or other means to move laterally within the network and gain access to the organization's ERP system.
7. Use the organization's ERP system to extract sensitive data, such as financial records or customer information.
8. Use the stolen data to create false transactions or to manipulate the organization's business processes.
9. Attempt to cover your tracks by deleting or modifying log files or other evidence of the attack.
10. Use a variety of evasion techniques to avoid detection, such as using encrypted communication channels or using multiple command and control servers.
11. Report your findings and recommendations to the organization's leadership, including any actions that should be taken to remediate the vulnerabilities and weaknesses that were exploited.
This attack scenario is similar to a real-world APT in that it involves a sustained, targeted attack on the organization's ERP system. The attacker uses a combination of tactics, techniques, and procedures to gain initial access to the network and then moves laterally to gain access to the organization's ERP system. The attacker uses the ERP system to extract sensitive data and then attempts to cover their tracks. The goal of the attack is to remain undetected for as long as possible and to cause as much damage as possible. The attack scenario would provide valuable information to the organization's leadership and could be used to improve the
### Examples
There have been several real-world advanced persistent threat (APT) attacks that have targeted enterprise resource planning (ERP) systems. Some examples of threat actors who have been known to conduct such attacks include:
- APT10: APT10, also known as Stone Panda, is a Chinese state-sponsored hacking group that has been active since at least 2009. APT10 has been known to target ERP systems, among other types of systems, in order to steal sensitive data and intellectual property.
- APT28: APT28, also known as Fancy Bear, is a Russian state-sponsored hacking group that has been active since at least 2007. APT28 has been known to target ERP systems, among other types of systems, in order to steal sensitive data and intellectual property.
- Lazarus Group: The Lazarus Group is a North Korean state-sponsored hacking group that has been active since at least 2009. The Lazarus Group has been known to target ERP systems, among other types of systems, in order to steal sensitive data and disrupt operations.
These are just a few examples of threat actors who have been known to conduct APT attacks against ERP systems. There are many other threat actors who have the capability and the motivation to conduct such attacks, including nation-state sponsored hacking groups, criminal organizations, and hacktivist groups.
## CRM
An attack scenario for an internal red team to target customer relationship management (CRM) systems could involve the following five steps:
1. Identify the organization's CRM system and gather information about its architecture, features, and security controls. This may involve researching the organization's website, speaking with employees, or conducting network or port scans.
2. Conduct a security assessment of the organization's CRM system to identify vulnerabilities and weaknesses. This may involve using automated tools to scan the organization's CRM system for known vulnerabilities, or manually testing the system's security controls to identify potential weaknesses.
3. Identify and exploit a weakness in the organization's CRM system, such as an unpatched vulnerability or a misconfigured security setting. This may involve using known exploits or custom-developed tools to gain access to the CRM system, or using social engineering tactics to trick employees into providing access to the system.
4. Once inside the CRM system, use a variety of techniques to extract sensitive data, such as customer information, sales data, or marketing plans. This may involve using SQL injection attacks to access the organization's database, or using tools to scrape data from the organization's CRM system.
5. Use the stolen data to create false customer accounts or to manipulate the organization's customer records. This may involve creating new customer accounts with fake information, or modifying existing customer records to change contact information or other details.
### Examples
There have been several real-world advanced persistent threat (APT) attacks that have targeted customer relationship management (CRM) systems. Some examples of these attacks and the threat actors involved include:
- APT1: In 2011, the U.S. government indicted five members of APT1, a Chinese state-sponsored hacking group, for their involvement in a series of APT attacks against U.S. companies and organizations. One of the companies targeted by APT1 was a global manufacturer of computer hardware, which the hackers breached by compromising the company's CRM system and stealing sensitive data, including email addresses and other personal information of the company's customers.
- APT12: In 2013, a security firm published a report detailing an APT attack against a global law firm, which was attributed to APT12, a Chinese state-sponsored hacking group. The attack involved the use of a custom-developed malware tool called "Greasy Panda" to gain access to the law firm's CRM system, where the hackers were able to steal sensitive data, including confidential client information.
- APT29: In 2015, a security firm published a report detailing an APT attack against a large U.S. government agency, which was attributed to APT29, a Russian state-sponsored hacking group. The attack involved the use of spear phishing emails to trick agency employees into visiting a compromised website, where they were infected with malware that gave the attackers access to the agency's network. Once inside the network, the attackers used a variety of techniques to move laterally and gain access to the agency's CRM system. Once they had access to the CRM system, the attackers were able to extract sensitive data, including information about the agency's clients and their personal information. The attackers used the stolen data to create false client accounts and to manipulate the agency's customer records.
Overall, these examples demonstrate the potential impact of APT attacks against CRM systems, and the sophisticated tactics, techniques, and procedures that threat actors use to conduct such attacks. CRM systems often contain a wealth of sensitive information about an organization's customers, making them a prime target for attackers who are looking to steal sensitive data or to disrupt the organization's operations.
## BI
An attack scenario for an internal red team to target business intelligence (BI) systems could involve the following five steps:
1. Identify the organization's BI system and gather information about its architecture, features, and security controls. For example, you may research the organization's website to determine which BI software they are using, or you may speak with employees to learn more about how the system is used and how it is secured.
2. Conduct a security assessment of the organization's BI system to identify vulnerabilities and weaknesses. This may involve using automated tools, such as network scanners or vulnerability scanners, to identify potential vulnerabilities in the BI system. You may also conduct manual tests, such as attempting to access the system with default or weak credentials, to identify potential weaknesses in the system's security controls.
3. Identify and exploit a weakness in the organization's BI system, such as an unpatched vulnerability or a misconfigured security setting. For example, you may use a known exploit to gain access to the BI system through a vulnerable web application, or you may use social engineering tactics to trick an employee into providing you with access to the system.
4. Once inside the BI system, use a variety of techniques to extract sensitive data, such as financial records, sales data, or marketing plans. This may involve using SQL injection attacks to access the organization's database, or using tools to scrape data from the organization's BI system.
5. Use the stolen data to create false reports or to manipulate the organization's business intelligence data. This may involve creating new reports with fake data, or modifying existing reports to change the results or conclusions. For example, you may create a false sales report that shows inflated revenue numbers, or you may modify an existing report to show incorrect data about the organization's customers.
### Examples
There have been several real-world advanced persistent threat (APT) attacks that have targeted business intelligence (BI) systems. Some examples of these attacks and the threat actors involved include:
- APT1: In 2011, the U.S. government indicted five members of APT1, a Chinese state-sponsored hacking group, for their involvement in a series of APT attacks against U.S. companies and organizations. One of the companies targeted by APT1 was a global manufacturer of computer hardware, which the hackers compromised by gaining access to the company's BI system and stealing sensitive data, including financial records and sales data.
- APT29: In 2015, a security firm published a report detailing an APT attack against a large U.S. government agency, which was attributed to APT29, a Russian state-sponsored hacking group. The attack involved the use of spear phishing emails to trick agency employees into visiting a compromised website, where they were infected with malware that gave the attackers access to the agency's network. Once inside the network, the attackers used a variety of techniques to move laterally and gain access to the agency's BI system, where they were able to steal sensitive data, including financial records and intelligence reports.
- APT28: In 2016, a security firm published a report detailing an APT attack against a U.S. defense contractor, which was attributed to APT28, a Russian state-sponsored hacking group. The attack involved the use of a custom-developed malware tool called "Sednit" to gain access to the contractor's network, where the hackers were able to steal sensitive data, including financial records and sales data from the contractor's BI system.
Overall, these examples demonstrate the potential impact of APT attacks against BI systems, and the sophisticated tactics, techniques, and procedures that threat actors use to conduct such attacks. BI systems often contain a wealth of sensitive data about an organization's financial and operational performance, making them a prime target for attackers who are looking to steal sensitive data or to disrupt the organization's operations.**